The Future of Security: Checking Out the Most Recent Trends in Electronic Safety And Security Technologies
In the world of security and protection, the landscape is continuously developing, driven by technical innovations that push the borders of what is possible. Electronic safety modern technologies have actually become increasingly sophisticated, offering cutting-edge options to deal with the ever-growing difficulties faced by individuals and companies alike. From biometric verification to the integration of expert system and artificial intelligence, these fads hold the pledge of enhancing safety actions in unprecedented means. As we browse through this detailed internet of innovations, one can not assist but question just how these modern technologies will form the future of safety and security and security, setting the stage for a brand-new period of defense and durability (BQT Locks).
Surge of Biometric Authentication
With the raising requirement for secure and convenient authentication methods, the rise of biometric verification has actually transformed the means individuals accessibility and safeguard their sensitive info. Biometric authentication utilizes special organic attributes such as fingerprints, face features, iris patterns, voice recognition, and even behavior characteristics for identity confirmation. This innovation provides a more reputable and secure technique compared to traditional passwords or PINs, as biometric data is unbelievably difficult to reproduce or take.
Among the key benefits of biometric verification is its ease. Customers no longer need to remember intricate passwords or stress about shedding gain access to due to forgotten qualifications. By merely utilizing a part of their body for verification, individuals can swiftly and securely access their devices, accounts, or physical spaces.
Additionally, biometric authentication improves safety and security by supplying a much more robust defense against unauthorized gain access to. With biometric markers being unique to each individual, the threat of identity burglary or unapproved access is considerably lowered. This heightened level of security is especially critical in sectors such as money, health care, and government where safeguarding delicate information is paramount.
Assimilation of AI and Machine Understanding
The advancement of digital security innovations, exhibited by the increase of biometric verification, has paved the method for advancements in the combination of AI and Artificial intelligence for enhanced identification and security mechanisms. By leveraging AI algorithms and Artificial intelligence designs, digital safety systems can now analyze huge amounts of data to discover patterns, anomalies, and prospective risks in real-time. These modern technologies can adapt to advancing safety dangers and supply positive reactions to alleviate threats efficiently.
One significant application of AI and Machine Learning in digital safety and security remains in predictive analytics, where historic data is utilized to anticipate possible safety and security breaches or cyber-attacks. This positive method enables safety systems to expect and protect against dangers before they occur, boosting general precaution. In addition, AI-powered security systems can smartly monitor and evaluate video clip feeds to determine dubious tasks or people, enhancing reaction times and reducing incorrect alarm systems.
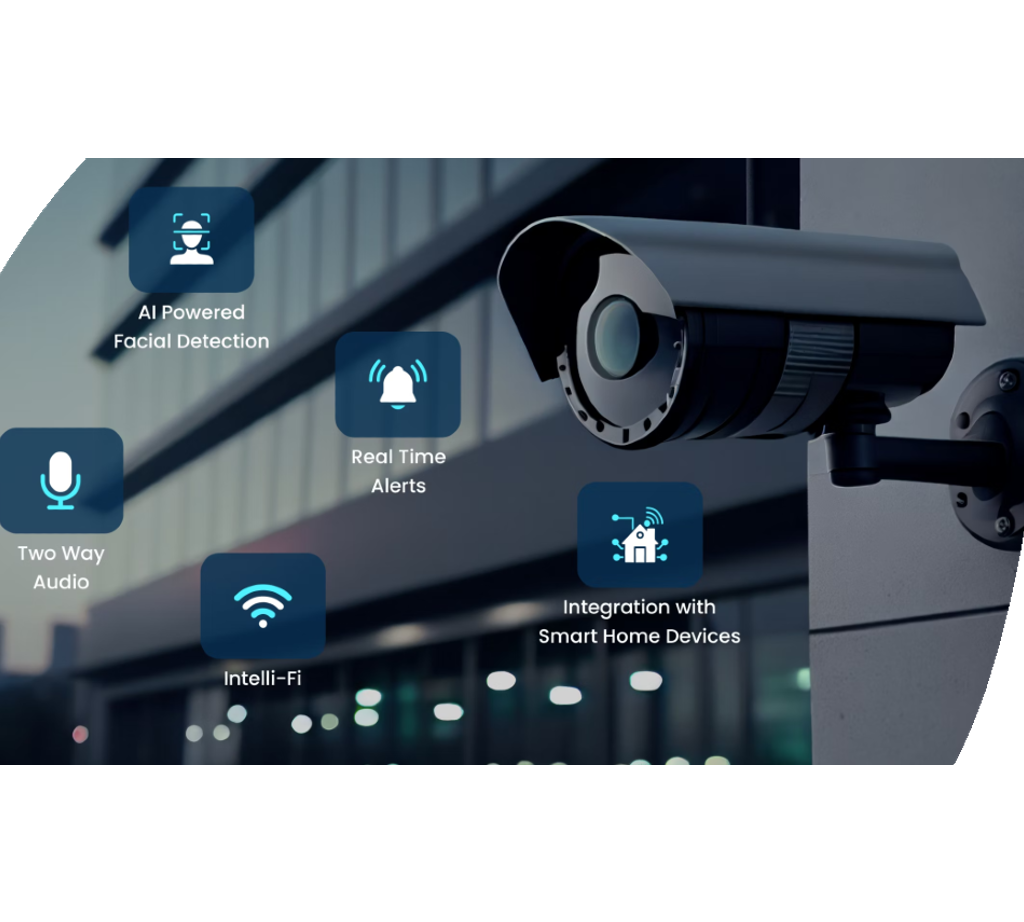
IoT and Smart Protection Tools
Developments in electronic safety and security modern technologies have see it here actually led to the emergence of IoT and Smart Safety Gadgets, reinventing the way security systems operate. The Net of Points (IoT) has actually made it possible for protection gadgets to be adjoined and from another location easily accessible, offering improved tracking and control capacities. Smart Safety Tools, such as wise cams, door locks, and activity sensing units, are geared up with functionalities like real-time notifies, two-way interaction, and combination with various other wise home systems.
Among the substantial advantages of IoT and Smart Protection Tools is the ability to provide individuals with smooth accessibility to their security systems via mobile phones or other internet-connected devices. This convenience enables remote tracking, arming, and disarming of safety and security systems from anywhere, providing home owners with comfort and adaptability. Moreover, these tools commonly incorporate innovative features like face recognition, geofencing, and activity pattern recognition to enhance total protection degrees.
As IoT remains to evolve, the combination of expert system and maker learning algorithms right into Smart Protection Tools is anticipated to further enhance discovery precision and personalization alternatives, making electronic protection systems also much more reliable and reputable.
Cloud-Based Security Solutions
Arising as a crucial facet of contemporary digital security facilities, Cloud-Based Security Solutions use unrivaled versatility and scalability in safeguarding digital properties. Cloud-based safety and security options enable remote surveillance, real-time notifies, and streamlined monitoring of safety systems from any type of place with a web link.
Furthermore, cloud-based protection solutions supply automated software program updates and maintenance, guaranteeing that security systems are constantly current with the most up to date protections versus arising dangers. The scalability of cloud-based options permits companies to conveniently broaden their safety infrastructure as needed, accommodating growth and adjustments in protection requirements. In addition, cloud-based protection solutions commonly come with integrated redundancy and disaster recuperation capacities, reducing the risk of data loss or system downtime. Generally, cloud-based safety services stand for an economical and reliable way see this here for services to boost their security stance and secure their digital assets.
Focus on Cybersecurity Measures
With the raising refinement of cyber hazards, businesses are placing a paramount emphasis on bolstering their cybersecurity steps. BQT Biometrics Australia. As innovation advances, so do the techniques utilized by cybercriminals to breach systems and swipe delicate information. This click to find out more has prompted organizations to invest greatly in cybersecurity procedures to protect their information, networks, and systems from malicious strikes
Among the crucial fads in cybersecurity is the fostering of innovative encryption procedures to safeguard data both at remainder and en route. File encryption assists to make certain that even if information is intercepted, it remains unreadable and protected. Furthermore, the execution of multi-factor verification has actually ended up being significantly typical to include an added layer of safety and security and validate the identifications of users accessing delicate info.
Verdict
